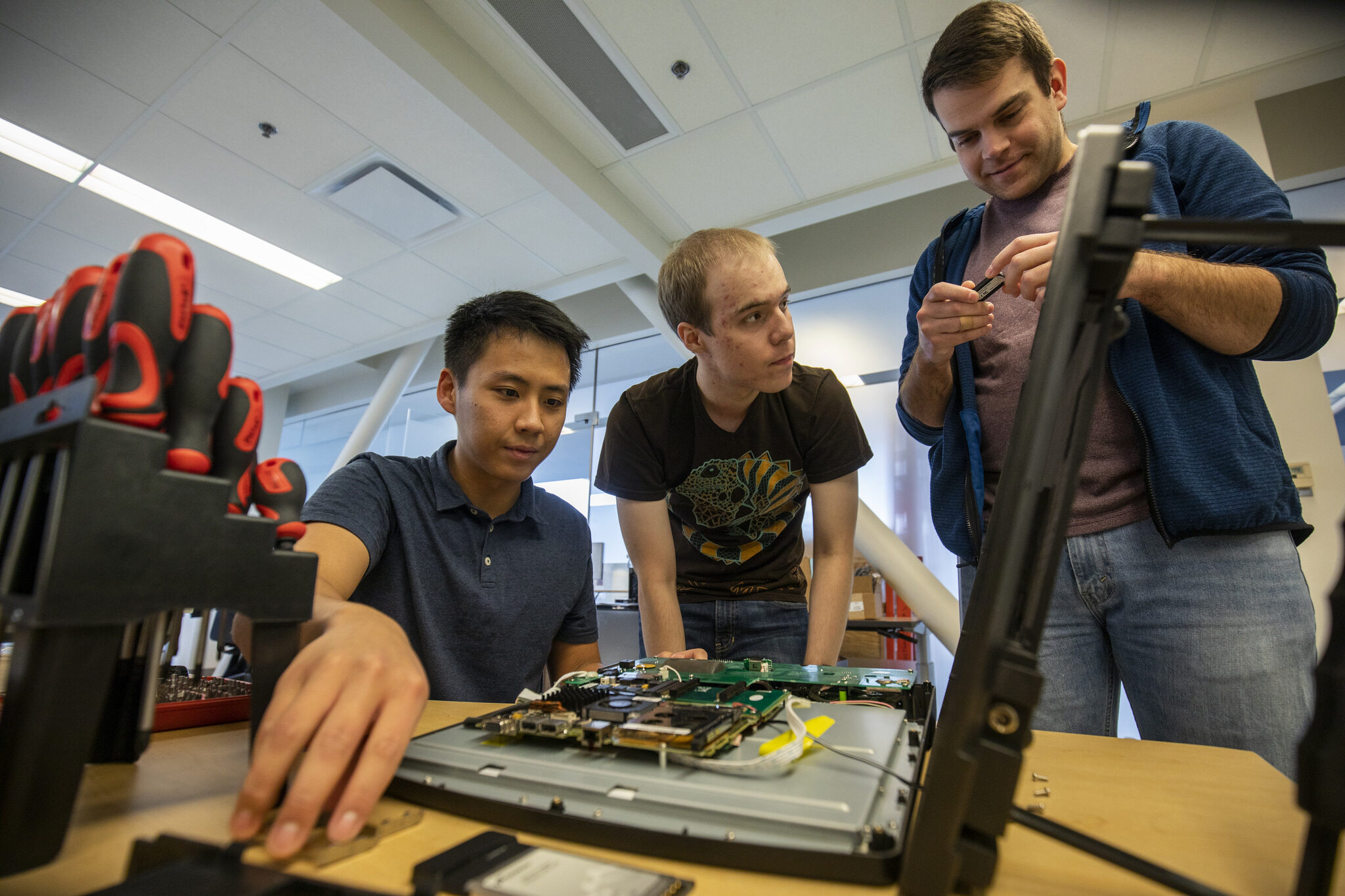
PhD Student Matt Bernhard (right) along with Victor Ongkowijaya and Stephen Nurushev, both Undergrads in Electrical Engineering and Computer Science, work on extracting data from used voting machines acquired through Ebay One of the machines that the students broke down found voting record data dating from 2004–2014. These machines are still widely used in Louisiana and South Carolina. A new special topics course on election security taught by CSE Professor J. Alex Haldermand and Bernhard provides students with a deep examination of the past, present, and future of US elections, informed by perspectives from computer security, tech policy, human factors, and more. Photo by Robert Coelius/Michigan Engineering, Communications and marketing
Trustworthy elections have been a cornerstone of American democracy. Now that we’re squarely in the digital age, voting machines have largely replaced paper ballots – but many of these machines are susceptible to errors, manipulation, or hacking, raising concerns about the integrity of election results.
Prof. J. Alex Halderman has been at the forefront of exposing vulnerabilities in electronic voting systems around the world. By pointing to root causes behind these shortcomings, he hopes to “harden” the voting process, ensuring that votes are properly tabulated and preventing an erosion of trust in our electoral system.
This Fall, Prof. Halderman and CSE PhD student Matt Bernhard are teaching a new special topics course on election cybersecurity, providing students with a deep examination of the past, present, and future of US elections with perspectives from computer security, tech policy, human factors, and more.
The course aims to give students a real-world, hands-on application to deepen their experience from previous cybersecurity coursework. They cover a number of practical challenges and vulnerabilities facing the American election system: safeguards for election infrastructure; the rise of digital information warfare against political campaigns; legal and regulatory structures that impact election security at federal, state, and local levels; and efforts to change technology and policy to strengthen security.
“Election security is a severely understudied field, and one of our goals with the course is to inspire students to do this work themselves,” Bernhard says. “I also think it’s a great way to engage students in our democracy; unfortunately young people in this country don’t participate enough, so I hope our course helps inspire our students to become more engaged in that arena.”
Students in the course work on a group final project throughout the semester, applying their coursework to the many pain points in the voting system. Students are examining everything from manipulation of voter registration systems to alternative physical seals on the voting machines themselves.
Attention was brought to the latter by Bernhard’s well-documented use of a soda can to break the plastic seals that hold the machines shut at polling places. These ties and a few screws are all that keep the machine locked down against physical tampering.
In one project for the course, undergrads Victor Ongkowijaya and Stephen Nurushev are working on extracting data from used voting machines. Bernhard acquired voting machines from precincts in Ohio, containing voting record data dating from 2004–2014. One of the machines that the students broke down is still used statewide in Louisiana and South Carolina.
Ongkowijaya and Nurushev found that the machines are made from a variety of second-hand and consumer parts, with standard laptop memory and hard drive storage. The machines are programmed with a common USB thumb drive, clipped in place on the machine with plastic when in use. Using software called Autopsy, Ongkowijaya and Nurushev extracted data from the voting machine’s hard drive and USB drive, very little of which was encrypted. Among some of the junk data found on the consumer-grade USB drive were MP3 files and music videos.

Victor Ongkowijaya and Stephen Nurushev, both Undergrad Students in Electrical Engineering and Computer Science, work on extracting data from used voting machines acquired through Ebay for their final project in a new special topics course on election security taught by CSE Professor J. Alex Haldermand and PhD Candidate Matt Bernhard. This course provides students with a deep examination of the past, present, and future of US elections, informed by perspectives from computer security, tech policy, human factors, and more. Photo by Robert Coelius/Michigan Engineering, Communications and Marketing
“Strengthening election cybersecurity is essential for safeguarding democracy,” Halderman says about the course. Attacks against recent elections in the U.S. and Europe demonstrate that cybercriminals are becoming more aggressive, even as campaigning and voting become increasingly reliant on vulnerable computer and networks.
Election cybersecurity raises complex challenges at the intersection of computer science, law and public policy, politics, and international affairs. Students from across these disciplines were encouraged to join the course.


